In our Turris project, in addition to taking preventive measures that would protect users against various attacks from the outside, we also do other activities. Those include contacting clients from whose side we detect attempts to connect to IP addresses that are known to be botnets’ command and control centers, or blocking IP addresses that are used by websites to perform malicious attacks on users. During that time we have seen some curious incidents that I would like to briefly outline here.
Analysis of anomalies
Two incidents are worth mentioning here. One is an anomaly, which concerned Turris routers only within the network of one particular ISP. It was connecting to the port 123, which is a NTP port. Therefore, we arranged with the owner and set a trap on one of the routers connected to the same network and waited for the scanning to occur again. The captured data confirmed our expectations, that is that someone is testing the machines for vulnerabilities allowing to cause a NTP amplification attack using the monlist command.
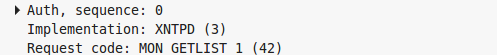
Data captured by our trap for the suspect
At that point, we only needed to verify whether it was a potential attacker, who is looking for vulnerable machines for future attacks on someone else, or whether it was only a testing mechanism of the ISP. After some time, the ISP fortunately confirmed that it was the latter; a responsible provider monitoring potential weaknesses of its network.
Another interesting anomaly concerned the port 32764. We suspected that these access attempts could be related to the backdoor in some routers found earlier, but we were surprised by the frequency of the attempts. Later it turned out that it was probably a new malware that spreads in this way. By now we have already detected first attempts of the scan also from IP addresses in the Czech Republic, so now we will try to obtain samples of this new malware.
Botnet warning system
The next area is our service that allows us to warn Turris router owners, if we detect that some device of their network attempts to connect to a known botnet control center. Probably the most interesting case was the one when Turris helped detect malware on a device connected to a totally different network. How could it have happened? It started with us notifying the owner of the router of the fact that a device in their network has connected to the Zeus botnet center. The owner told us that they were running a NAS on a minimalist version of Linux. However, they said that he has a VPN configured on the device and that at the time a friend’s Windows XP has been connected to it. The subsequent antivirus check of the affected computer with WinXP actually discovered viruses.
We launched the service in late May and have since discovered fourteen infected computers using this method. During this trial run, one more interesting thing has come up. Specifically, the case of a user who had previously been informed by their ISP of a possible infected PC on their network. Since the notification lacked precise identification of the device, the user had dismissed it. Only afterwards, the information from the Turris router pointed to the specific machine on the user’s network.
Dangerous website blocking
We are also working on a list of IP addresses that are currently used for attacks through web browsers. We acquire these IP addresses by analyzing infected websites in the .CZ domain zone that can lead to a specific server abroad, which was used to attack the visitors’ computers. In order to protect the users involved in the Turris project, these IP addresses are then temporarily monitored or blocked according to the degree of certainty that the IP address constitutes a clear threat and is not being used for any other purpose. There is a curious fact related to it. For example, in the last two weeks, the Turris project blocked 259 attempts of access to dangerous IP addresses. I do not believe users of Turris ignored their browsers’ warnings about a dangerous site as many times.
A standard browser warning that Turris users would had to ignore 259 times during the past two weeks
I personally believe that a large proportion of these 259 blocked attempts was conducted through an infected website, which is not yet in the database used by browsers. The things is that a link to a truly malicious website is often embedded into multiple hacked sites at once using iframe. It is likely that some of these websites are not discovered during the first days and users can be protected only by periodically updating their software and, in case of the Turris router users, also by our analytical work on dangerous websites.
Hot news of the recent days
In the short time between finishing and publishing of this blogpost, two more interesting incidents took place. One is the announcement of spying on users of Xiaomi products, which we have so far responded to only by logging of accesses to api.account.xiaomi.com. Unfortunately, apart from obtaining private user data, this interface is used for regular customer service for users of tablet or mobile phones from this brand. At the moment, we are just monitoring the situation. It is clear from the number of accesses, that the brand is relatively popular. The question is whether we should deal with these accesses somehow and try to contact users with information about the possible risks associated with the use of these devices. We would be glad if you left your opinion on this issue in the discussion below.
The second event of interest concerns the new Synolocker malware that attacks Synology NAS servers. It encrypts the hard drive of an attacked device and demands “a bail” of thousands of crowns for decryption. Thanks to the large spread of the Turris routers in different networks and well-functioning anomaly detection, we managed to get some interesting data regarding accesses to the ports with the vulnerable application misused for spreading this malware. In the course of investigation, the Synology company became interested in this data that might help identify the attackers. Hopefully, the established cooperation will help to find individuals responsible for the attack. Those were some interesting incidents that we have dealt with in cooperation on the Turris project. I would say it is quite a promising start!