In the next release of Turris OS, we would like to give our users the possibility to play a more active part in detection of network attacks. The first of the new functions is SSH honeypot which lures the attacker into a virtual environment where we can then observe his activity. This method will be more thoroughly described in a separate blog post planned for the near future. The second addition is less ambitious, but much simpler and still very useful. It is stripped down version of a honeypot which we internally call a “minipot”. In contrast to the normal honeypot which lets any attacker in with any password, our minipot just pretends that there is the possibility of logging in, and collects the supplied user names and passwords.
Even though this approach does not bring as much data, it is still very useful when compared to, for example, simple observation of firewall logs. One of the advantages is that we can be more sure about the attackers malicious intent. We can also use the supplied names and passwords to get a picture about the attacker, and even to uncover groups of similarly behaving attackers.
Because we have found that such analysis brings interesting insights even with the small number of routers that we use for testing of new pre-production releases, we decided to publish the results in advance of the minipot being released to the users. We assume that the results will get even more interesting once all routers are used.
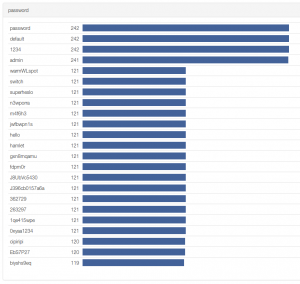
It will probably not surprise you that the most often tried combinations of login and password are root/root and admin/admin. On the other hand, how many attackers would you guess try the password “J8UbVc5430”? One, two? And what if you find out that the number is more than a hundred? Such information might lead one to dig a little deeper into the matter, which is exactly what we did.
We used a method called cosine similarity, which is used for example to asses similarity between texts, to identify groups of similarly behaving attackers. Using this method, several groups using different sets tested credentials were identified, which means that there might be the same person or at least tool behind the individual groups. Probably the most interesting group was one formed by 121 distinct IP addresses (number from May 22, 2015), which used a dictionary of passwords containing besides the above mentioned “J8UbVc5430” also “0xyaa1234”, “biyshs9eq” and other interesting combinations.
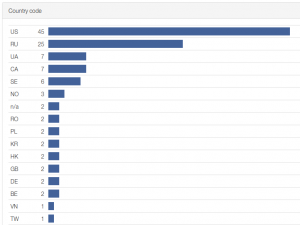
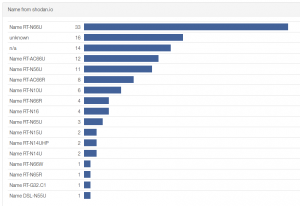
This strange list of passwords made us curious to find more about the group of attackers. The mystery of where did the passwords come from resolved itself quickly when we found several of the passwords on the internet in various documents from past successful attacks. Finding out what do the attackers have in common was more demanding. We started by doing a country and ISP search for the IP addresses, but this did not reveal anything of much use. It wasn’t until we tried additional data from shodan.io, that we found the pattern. The devices behind the detected IP addresses were in most cases home routers made by ASUS. And from models which were shown in the past to contains serious security flaws (Arstechnica 2014, Securityweek 2015).
When we combine this information with the fact that all the routers are trying the passwords in the same order and from time to time add one new at roughly the same time, we can be almost certain that they are part of one botnet run by one attacker. Because we used data from only a few routers in this analysis, it is probably too soon to make any conclusions about the size of the botnet. We will certainly keep monitoring the situation and hopefully get more data once our minipot is distributed to a larger number of routers.
In the meantime, I would like to warn that the frequency of attacks on routers with a public IP address via telnet is about once in 3 minutes. This means that when you connect a router with default credentials root/root and telnet open to the internet, you might not change the password in time before someone installs a backdoor on it under your hands.
We can only hope that manufacturers do not have such obvious security holes in their new systems anymore. And also that the users will not open them themselves by tinkering with unknown router settings 🙂 .
Update 2015-05-25 7:30: Over the weekend, the number of unique IP addresses trying the above mentioned passwords rose to 183.