In the previous two blog posts about project Turris, we described how a telnet “minipot” helped us to uncover a possible botnet consisting mainly of home routers from ASUS (1, 2). In this article, we will describe one possible way how these devices might have been compromised.
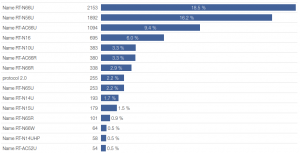
When we found out that there had been more than a hundred different devices trying to login to Telnet on our development routers using the same set of non-trivial passwords, we decided to have a closer look at this phenomenon. We deployed the minipot to all Turris routers which led to much faster collection of new data, and we currently have more than 13 000 unique IP addresses (70% of which are routers from ASUS) which all use the same dictionary of passwords mentioned above. With the help of our colleagues from CSIRT.CZ, we have started to notify ISPs, in whose networks we have seen this activity, with the intent of getting more information. We have also installed a full-blown honeypot for Telnet in which we have already caught a few of the attackers belonging to this group. And last, but not least, we bought one of the router models which takes part in these attacks and made it available from the Internet in order to find out if and how it will be compromised.
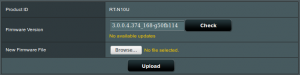
It was model RT-N10U, hw revision B1. Its firmware version 3.0.0.4.374_168 and we used the built-in check on the router to make sure that there is no more recent firmware available. Besides basic setup, we also set a new non-trivial password for the web interface.
In order to get as much information about possible attacks as possible, we turned off the firewall of the device. While this might seem unfair, it probably corresponds to the setup of many of the compromised routers as can be seen from the services available on them from the Internet.
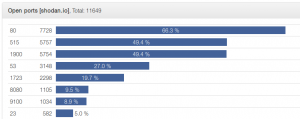
After this, we simply left the device in a separate subnetwork accessible from the Internet and recorded all traffic coming to and from the router. Besides the usual attempts to connect to WordPress admin or mysqladmin, we only saw a larger number of scans of uPnP on port 1900 in the first two weeks of this experiment. The situation changed this weekend when we recorded access to the web interface from Bulgaria which used the correct password. Because we did not observe any attempt to guess the password by brute force, we assumed the attacker must have somehow gotten the password directly from the router. Following further analysis, we found out that this password was indeed included in plain text in one of the previous answers from the devices. The URL was /error_page.htm and contained the following piece of javascript (the password was replaced by XXXXXXXXX):
if('1' == '0' || 'XXXXXXXXX' == 'admin')
setTimeout("parent.location = \"http://"+new_lan_ip+"/QIS_wizard.htm?flag=welcome\"", 2*1000);
else
setTimeout("parent.location = \"http://"+new_lan_ip+"/QIS_wizard.htm?flag=detect\"", 2*1000);
}
What is more, because the problem is in the web interface itself, the same behavior is observed even with the firewall turned on when administration web interface is available from the Internet.
We were of course shocked by this blatant security hole and did some further research. Simple search revealed that this bug was found and reported to ASUS no later than in February 2014. It was probably fixed in the meantime, but it is unclear if for all vulnerable models.
As mentioned above, our router shows that there is no more recent firmware available. But if we use Google, we can find out that there is a more recent version (3.0.0.4.376.3754) and we have from both the device’s behavior and the source code of the firmware confirmed that the issue was fixed there. This means that the automatic check for update included in the web interface not only does not work but is outright harmful because it brings a false sense of security. Thus even a security conscious user, willing to keep his/her device up-to-date and secure, might be fooled by this misleading information.
Conclusion
To summarize the above text: we bought a new router, checked that its firmware is up-to-date, changed the password to a secure one and made its web interface accessible from the Internet. In three weeks, the device was compromised because of a stupid security bug. We are not alone in this. On the Internet, there are at least 9000 other routers from the same manufacturer with the same problem. And these are only the ones we can see because they try to attack other computers via Telnet and can be thus easily spotted. In reality, it is likely that there are many more such devices that are compromised.
To finish on a slightly different note: this issue is not only one of routers from ASUS and one bad bug in the firmware. It is a more general problem of all devices connected to the Internet which are not properly maintained and kept up-to-date in many cases it is simply because of the price of the devices that, the manufacturer simply cannot offer new updates indefinitely. What is most disturbing for me about this issue is that these small devices might represent a huge hole into our networks and thus into our privacy.