For many years, our association has been running a service going by the acronym “ODVR” – Open DNSSEC Validating Resolvers. At times when DNSSEC was just beginning, we thought it was necessary to come up with an alternative to DNS resolvers provided by ISPs who introduced the validation support too slowly. Since then, we have offered a publicly available service that allows validation of domains using DNSSEC security even in those networks whose default DNS resolvers do not support this.
DNSSEC support has been growing steadily and it is becoming a standard. In 2008, none of the .cz domains were secured with this technology, while by the end of 2016 it was used by every other .cz domain. On the part of the DNS resolver operators, mostly the ISPs, the situation is similar, although they were always falling behind. As can be seen from Geoff Huston’s (APNIC) statistics, the DNSSEC support at DNS resolvers providing services for the Czech Republic now exceeds 40%. This number applies specifically to the RSA encryption algorithm, which is the predecessor of the more advanced ECDSA algorithm, to which a gradual transition is being made. Its support is lower (see chart below), but there is also a growing support trend. Since November 2016, ECDSA validation support in the Czech Republic has increased by 6% to today’s almost 36%.
Although the availability of DNSSEC from ISPs keeps improving, most Internet users still do not validate with DNSSEC. ODVR is aimed at these users, and it will even allow them to use the already mentioned ECDSA.
Validation at our ODVR is secured by the Unbound recursive DNS server. We have been running it for a long time without major changes with recommended settings. The most interesting features of our configuration are:
- Unbound holds expired signatures for 10% of their validity period (expiration-inception). As records can be signed with a validity period of several days, weeks, or even months, the minimum and maximum times for holding an expired signature are also defined. In our configuration, the minimum time is set for 1 hour, while the maximum is 24 hours. I have recently responded to a query about the “malfunction” of validation in case of signature expiration and I had to go through the Unbound project documentation to find this explanation.
- Unbound forbids the translation of records for which private IPv4 or IPv6 addresses are set, that is IP addresses from the following ranges: 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16, 169.254.0.0/16, fd00::/8 and fe80::/10. It is to protect the user from the so-called DNS Rebinding. Another reason is that the DNSSEC validator may consider these records false.
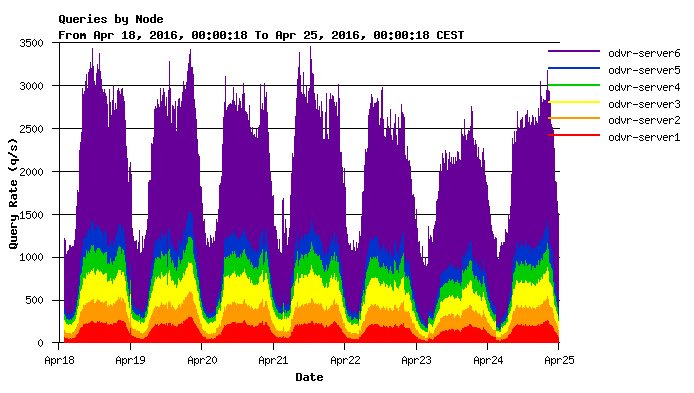
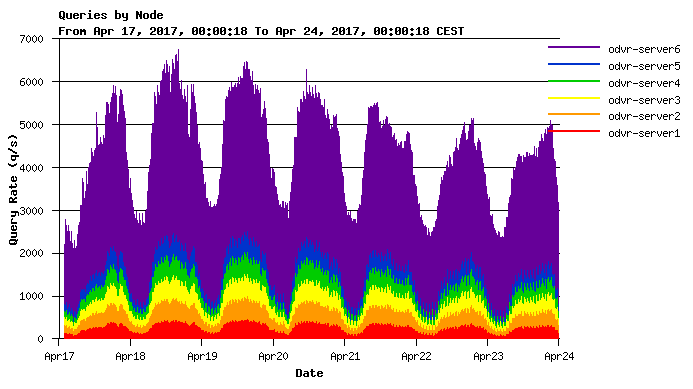
- ODVR resolvers are available on both IPv4 and IPv6 addresses. However, it is not just two servers. The ODVR is operated, like our authoritative DNS servers, within DNS anycast. In the Czech Republic alone, there are six of these servers, the operation of which is shown on the charts below. The charts also show how their use has increased over the course of one year.
- We are thinking about replacing of the Unbound by our KNOT Resolver. When we started with the ODVR, we had not had the KNOT Resolver.
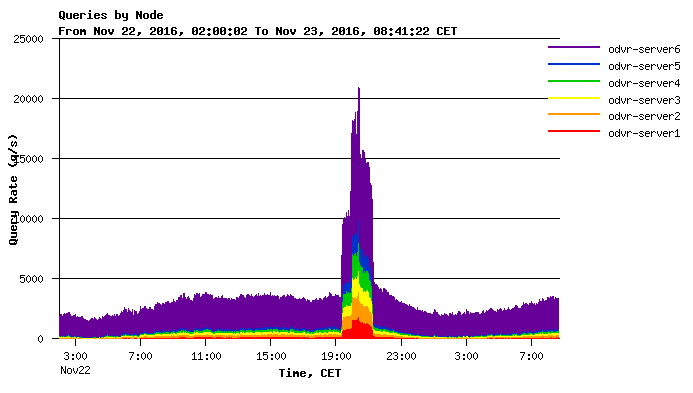
Apart from validation, ODVR might be used for other purposes. As we have long since pointed out in our initiative called The Censor is Coming, every Internet user may freely change their DNS resolver and if the law restricts the natural function of DNS for the ISPs, it will naturally lead to the increase in popularity of open resolvers – just like the popularity and use of our ODVR is growing; in peak times, it now processes more than 6,000 queries per second. And in some moments, the demand for ODVR is even significantly higher, for example when Google was down for two hours last year; see the following chart.