As we have reported several times, after massive upgrades of the anycast DNS for the .CZ domain zone in recent years and building of the 100GbE DNS infrastructure, we are now focusing more on targeted tuning of the anycast operation. For example, we try launching new DNS stacks in the locations of significant DNS traffic sources, both abroad and in Czechia. The launch of the DNS stack on the CESNET network at the beginning of April is the most recent fruit of this work.
We have launched the so-called ISP DNS Stack (sometimes called Local DNS anycast), which we have already written about on our blog, at CESNET, the network of the Czech academic e-infrastructure. The colleagues at CESNET have decided to deploy the ISP DNS Stack in their network in order to ensure greater security in the event of attacks on the DNS infrastructure and also to ensure a higher quality of service for their users.
ISP DNS stack is a designation for an instance of authoritative DNS server containing the .CZ zone in the internal network of a foreign entity, typically an internet service provider (hence the “ISP” part). We provide this service primarily to large ISPs (before CESNET, we have already launched it at Vodafone and Seznam.cz) who provide internet services to a larger number of customers and are therefore, from our point of view, an important user of DNS traffic. ISP DNS stack routes the anycast prefix of one of the CZ.NIC DNS anycasts to the network of such internet service provider, but the ISP is not allowed to route this prefix further upstream or to its peers. It is intended exclusively for the ISP network.
The main advantage of running such DNS instance from the perspective of the ISP is full DNS availability, even in the event of an attack on our public authoritative DNS servers. A user of the ISP network is not affected by such attack and the DNS service is fully available to them. As a side effect, the anycast design leads to a higher network throughput and faster query responses for the users of the network of the service provider with the installed ISP DNS stack.
The advantage for us is that if an attack on the ISP DNS stack is performed from the ISP internal network, the attack will be terminated on this DNS instance. The attack’s impact would not spread, which means that the public authoritative DNS servers would not be affected. This enables the ISP to immediately respond and deal with the attack, while rerouting the non-malicious DNS traffic to our public authoritative DNS servers.
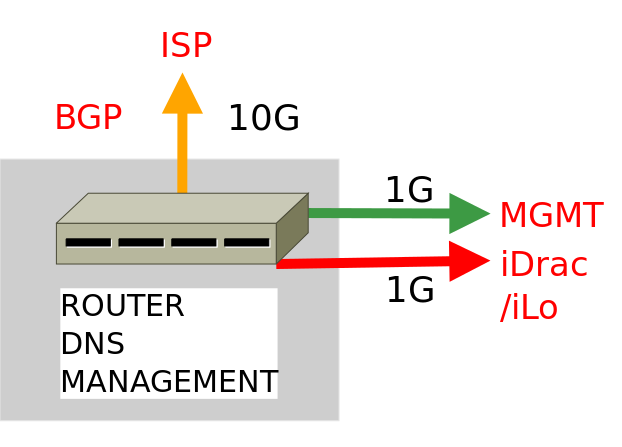
For most ISPs, and this is also true for CESNET, only one independent DNS server is sufficient to build an ISP DNS stack (see the image below), which would be able to process millions of DNS requests per second. This is the so-called basic version of the ISP DNS stack.
In the case of a higher number of DNS requests, we can extend the solution, for example to the so-called extended version of ISP DNS stack with separate services including five servers (3x DNS server, 1x management and monitoring server, 1x router), which can serve three times larger DNS traffic.
The CESNET ISP DNS stack is located in the ČRa Tower data center in Žižkov, Prague and runs on a Dell PowerEdge R640 server. It features two 8-core 2.10 GHz Intel Xeon Silver 4110 CPUs with Hyper-Threading. It also has 32GB RAM, a HW disk controller, 3x 300GB SAS 15k drives (one of which is used as a hot spare), an Intel i350 dual-port 1GbE network adapter and an Intel X710 SFP+ dual-port 10GbE network adapter. We are glad that here we also managed to maintain the diversity of vendor and server model, as previous ISP DNS stacks use either HPE ProLiant or an older model of Dell PowerEdge server.
The server has the OOB server management interface and a MGMT interface (iDrac remote management) connected via 1GbE ports to the Internet. The iDrac interface is the only one filtered on the CESNET firewall exclusively to selected IP prefixes of CZ.NIC and is only available through IPv6. We filter the rest of the network interfaces ourselves using the Linux iptables firewall. The server is connected directly to the CESNET backbone infrastructure, to the router where the BGP connection is established. Communication with the DNS server takes place only from CESNET, where the DDoS attack protection is applied as well.
The server is in our exclusive administration and since it is located in a rack not physically accessible to our administrators, all matters related to the operation of hardware (monitoring, maintenance, etc.) are resolved by colleagues from CESNET. We take care of all software support. A LUKS-encrypted file system is a matter of course. The server is running Debian Linux 10, with Bird as a routing/BGP daemon and KNOT DNS as a DNS daemon. The server gets updates of the .CZ zone the standard way, using AXFR from our hidden-master DNS servers. The CESNET network is notified by the DNS anycast C (194.0.14.1/24 + 2001:678:11::1/48). This anycast has been selected intentionally for all ISP DNS stacks because it is not reported from any public DNS stack in the Czech Republic and is available exclusively from selected foreign locations.
We are very happy that the number of our ISP DNS stacks is growing, and we thank CESNET for the opportunity to cooperate in this area! For potential new participants, we have prepared a more detailed document (only in Czech) describing both technical details and operating costs. I just note that the discount for the networks involved in FENIX remains valid! However, we will be happy to welcome FENIX non-members, too! 🙂