Moving to April, we gained almost ten thousand more unique attackers on average, according to the Greylist. To provide even more context to the events, we added yet another interesting figure — the number of total incidents recorded.
But we haven’t stopped at that yet. As you can see, we added pie charts for minipot sources, actions, and their combinations. The majority of attackers target SMTP servers. Both connect and login actions for SMTP are so frequent that they almost overshadow other data. We might try to address that somehow in future reports. Similarly it is hard to see the bottom of the chart in Sentinel View, so it is good to be able to get some idea about them here. While Telnet is far behind SMTP, it is still the second‑most targeted service. As we said before, the protocol is either used by some old devices or devices that don’t prioritize security — those are definitely the most desirable target. With the move from the FTP protocol to various more secure options and CMSes, we can say that HTTP seems more interesting for attackers these days. The conclusion would be that you should never ever use Telnet and secure your HTTP with most attention to security.
In regards to port descriptions, we started enriching the information from Wikipedia with other sources. However, with the port number 37183 that had jumped up by more than 300 000%, we still have no idea what service is using this port. The port is from class of dynamic/private range, which means that it can be used with virtually any application. On the top, we see a drop by 28% for port 27032 from last month. This one is used with Steam applications. Apart from that we see a decrease in BitTorrent related ports (maybe people were torrenting less last month) and slight decrease in attacks on Windows Shares. But don’t get sloppy and keep your shares out of the Internet.
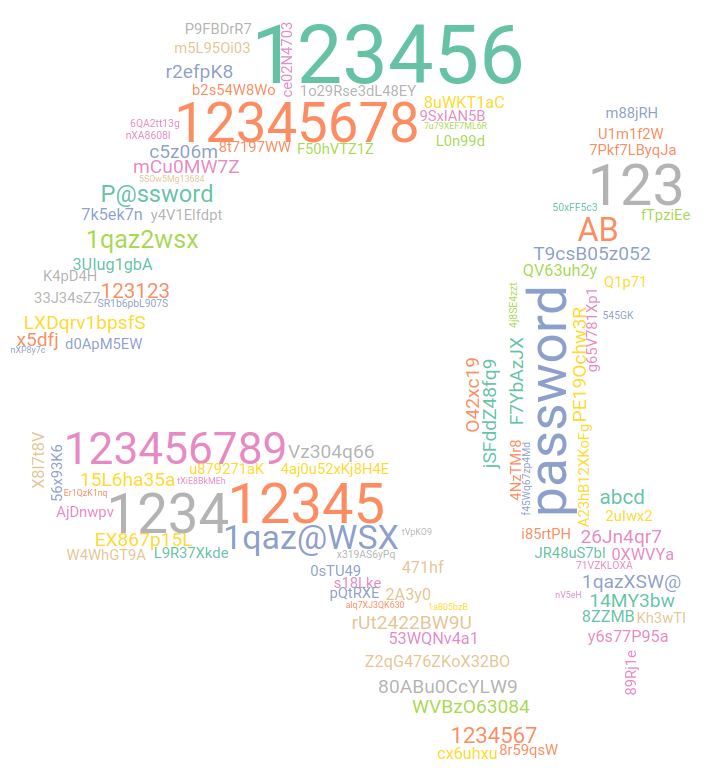
In passwords, the usual Iranian network is gone at last. We had high hopes for this month’s password list. But we run into someone trying random passwords. You can see it in the password lists. This time, it is just one very active attacker trying passwords starting at April 1st through April 3rd and every one of them approximately 14 thousand times. This IP belonged to a hosting provider. That might explain why the attack stopped quite shortly after it started. Someone on the provider side responded to the abuse report. Nevertheless we get a different noise this time. We might also rethink in the future how do we chart the top passwords to get more relevant data.