In early October, the international project “Cyber Security in the Danube Region” organized training for security teams operating within the region. As sharing of information and knowledge are essential in the field of security, I decided to write a post in which I would like to draw attention of the security community in the Czech Republic to two very interesting free tools.
As part of the training on malware analysis, Christian Wojner from the Austrian security team CERT.at presented his own tools ProcDOT and DensityScout. ProcDOT is a tool that is very useful for so-called behavioral analysis. Probably everyone who has ever analyzed malware for some operating systems from Microsoft or worked as an administrator of such system is already familiar with tools from the Sysinternals family. These tools can be used to reveal a lot of things about Windows operating system, from details about running processes through data on network communication or changes in the registry up to information about all processes automatically launched at the system startup. Output of one of these tools, the program Process Monitor, is used by the ProcDOT tool. It also uses PCAP files from programs such as WinDump or Wireshark as inputs.
Process Monitor allows you to monitor activity of the registry, the file system, processes, libraries, and network activity. Wireshark and WinDump are able to capture the entire network traffic. ProcDOT, using the information from files captured by the Process Monitor tool and PCAP files with network traffic, can draw a very clear chart showing the behavior and communication of a program.
In practice, we need to run a suspicious file on a PC with installed Process Monitor and WinDump. After a while, we save the gained information in both programs and use these files as input for the ProcDOT tool. Then we select the process of our interest. The following will appear.
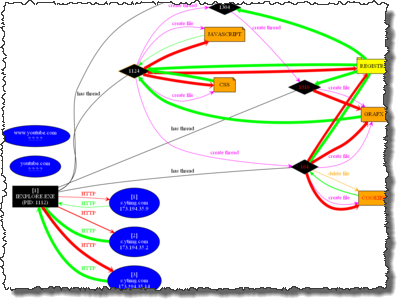
Source: http://www.procdot.com
ProcDOT will show us information about the files accessed by the process, Windows registry keys, network communication and other important parameters. This way you can quickly gain a comprehensive overview of the malware behavior and identify key phases of the infection course, for example, when the attack was through an unpatched browser weakness. It is possible to interactively browse individual parts or turn on the animation mode, which can help us understand the course of the infection in time. All these features make ProcDOT a very powerful tool for behavioral malware analysis.
The second tool, Density Scout, can be a useful aid when you have a computer with a suspected malware attack and conventional detection methods fail. This tool scans all files in the selected folder and calculates their entropy. It benefits from the typical behavior of malware authors who disguise their products in different ways. The thing is that tools for code obfuscation increase entropy of the generated files. On the other hand, most of the common executable files for Windows do not use these methods. Therefore, entropy of the potential malware differs from that of normal files. This is not a guaranteed method, but if you search for possible infection on your computer, it can help you identify suitable candidates for further analysis.
I hope the tools I introduced will help you in everyday practice. In our team, we plan to use them for analysis of the attacks identified in the project PROKI (Prediction and Protection against Cyber Incidents) implemented a part of the security research in the Czech Republic. But that’s a story for some other time.