In the last blogpost, I promised to write something about our new project PROKI. PROKI is the abbreviation of the Czech phrase for ‘prediction and protection against cyber incidents’ and in this project, our team set two goals for itself.
The first one is to collect data on security incidents from various sources. Some of them are fully public, for others some specific requirements need to be met. Anyway, this is a rich set of information about IP addresses hosting C&C servers, phishing sites and malware, IP addresses scanning the network on the Internet and IP addresses of computers belonging to a botnet. As a lot of such information remains unreported to the network, in which the problem has originated, one of the PROKI’s tasks will be notifying terminal networks of incidents that are related to them. Every once in a while — we are planning to decide how often it will be during the test run — a formatted report will be sent to the administrators of the network in question, from which they will learn about all the incidents observed during that period that somehow related to their network.
The second goal is a feature enabling to scan the incidents according to the set parameters that will allow us to look at incidents and especially the links between them from new angles. It will allow the incidents to be filtered by IP address, specific address blocks, country of “origin”, ports, number of the incident repetition and other parameters. In subsequent phases, we plan to add the option of detailed IP address view. This mode will include the additional data drawn from other sources such as various IP reputation databases, the VirusTotal database or the PassiveDNS system.
The system currently operates in the mode testing the viability of the proposed solution, which at its core involves the use of the open-source IntelMQ tools, ElasticSearch and Kibana. These cornerstones will be gradually complemented by further functions that were intended to be included in the stage of design and analysis of existing solutions. It needs to be added that our solution will also be available for free use.
As I wrote above, currently we are testing the viability of the proposed solution. At this pre-pilot stage, we have already involved several major players, including ISPs and hosting companies. In addition, we have also begun to test the analytical tool itself. During the current pre-testing, the system is running on hardware that does not allow us to perform a more complex analysis, but below you can see at least a little sneak peek.
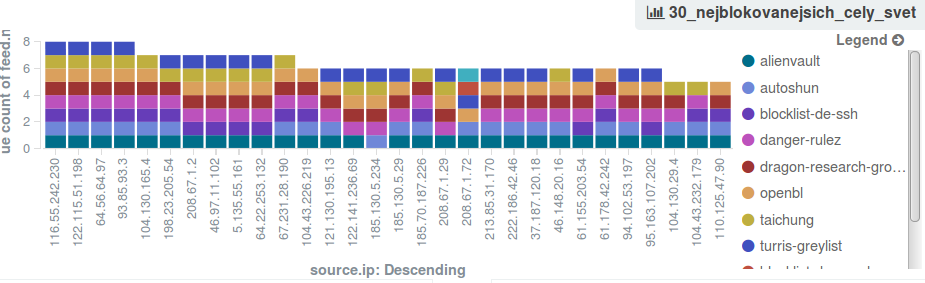
PROKI output: 30_most_blocked_worldwide
In this preview, we can see the 30 IP addresses topping the imaginary world ranking of IP addresses reported by the largest amount of resources over the past 10 days. Each color represents a source of information about naughty IP addresses, which listed the IP. At the very top, we can see data from the project Turris designated by the blue color, or IP addresses evaluated by the project as suspicious and included in the greylist. The colleagues from the project Turris can rejoice seeing the excellent job done by their algorithms that generate the greylist;, their calculations based on data from Turris obviously correspond with other databases aimed at gathering information about problematic IP addresses. It gets even more interesting if we try to enter one of the naughty IP addresses into a database such as PassiveDNS or virustotal.com. For now, it is necessary to perform queries manually, but as I wrote, the future integration of these additional information directly into the PROKI interface is on the list.
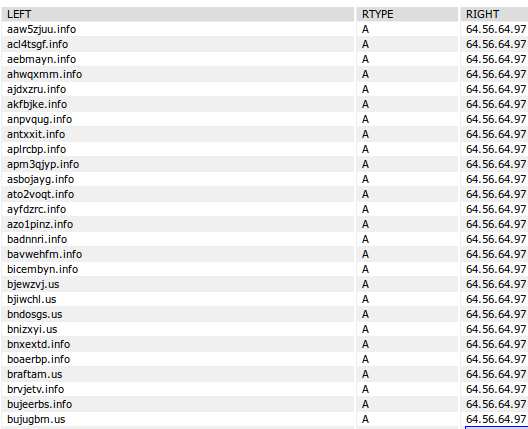
PassiveDNS: Some remarkable domain names here, don’t you think?
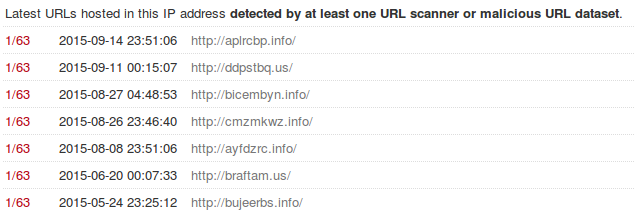
This is what virustotal sees for the same IP address.
PROKI is not just a tool searching for new perspectives on the existing data, but we are also expecting from it a more rapid detection of new C&C servers, phishing sites, sites spreading malware and other problems. This is thanks to connectedness to other tools that can tell us, for instance, where the domain that only days before was routing to the IP address that has been assessed as problematic is routing now, and thus show us where the harmful content was moved. In addition, PROKI will maintain history of problems with individual IP addresses and allow us, for example, to trace the networks that specialize on services for cyber criminals (yes, to our knowledge, there are such networks in the Czech Republic). It will also allow to check whether the IP address, the holder of which is under investigation for involvement in some attack, was not at the same time a member of a botnet, which would suddenly turn the accused into a victim. We should add that our project has been found so interesting that it was supported by the Security research program of the Czech Republic for the years 2015–2020.