Or, to be exact, you could welcome it last October, when we released its beta version. In the beginning, we were debugging it, while leaving the registration free, then came the stress test in the form of moving of all users of the Turris routers. We resolved all the issues and considered the suggestions, so nothing was in the way of launching HaaS — Honeypot as a Service.
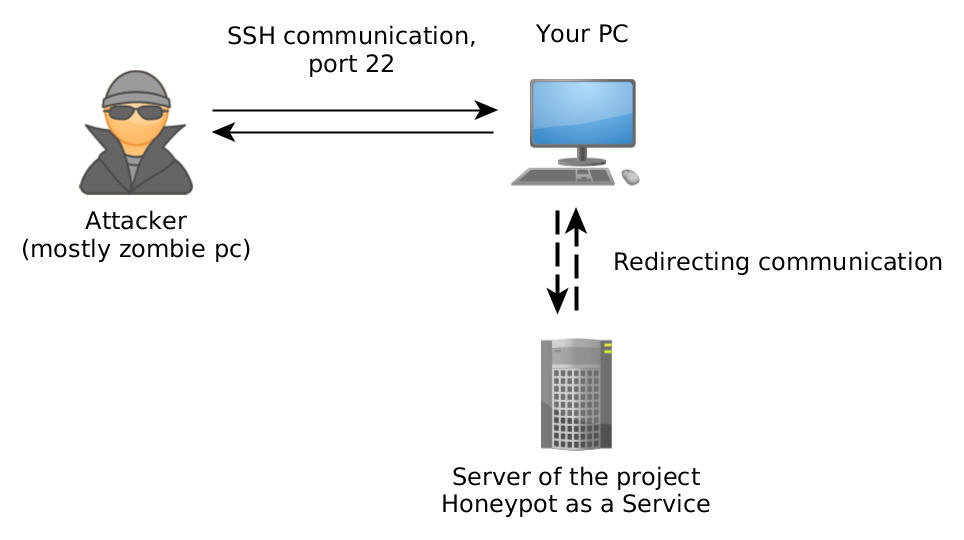
What is HaaS, and what is it for? Honeypot is a special application that simulates an operating system and allows potential attackers to log in to the end device through SSH and execute any commands or download malware. Installing such an application is not easy, and if any errors occur in it, it can become dangerous. That’s why we decided to take the security risk and make the honeypot available as a public service where Internet users can redirect attacks on their routers.
We’d love to say that all you have to do is to allow port 22 on your router and redirect it to our servers, but that’s not the case. However, we tried our best to make the solution easy to install and develop. Trust us, we spent at least a whole month choosing a proxy that would work for users. Why does it need a proxy? To solve just one small, but very important detail: it allows us to learn the attacker’s IP address, which is used to analyze the behavior of the attackers in order to detect new, yet unknown attacks.
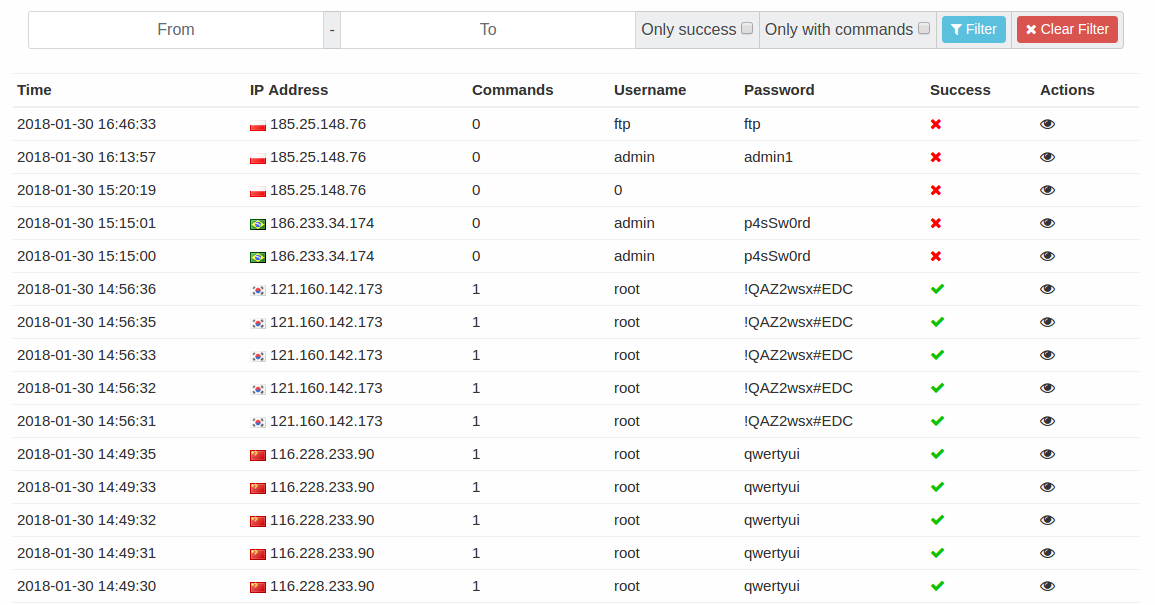
The good news is that we have a lot of data despite the short time of operation and problems in the beta phase. With ten thousand new SSH sessions per hour even with so few users (currently 1,600 active users), we will soon be pretty busy analyzing all this data. We will give it all we’ve got, because botnets executing rm -rf as first command frighten us and we must take care of them.
The collected data is used by the National Security Team CSIRT.CZ to investigate attacks from Czech IP addresses, which are then notified to the owners who are requested to remedy this. The largest number of attacks comes from China, so we are already cooperating with Taiwan to be able to intervene. We are working to establish cooperation with other security teams.
If you want to join the project, you can do so at haas.nic.cz, where you can register and follow the instructions to install HaaS proxy (available as deb and rpm packages, PyPI or just tar). If you are interested in data analysis, anonymized data is available on the Global Statistics page. The passwords that were used are not published intentionally, as we have recorded a few cases where a user accidentally got into their own honeypot.