In the newly released Turris OS 5.2 version, you can find Overview after logging in to web interface reForis. It provides you easily recognized status about the activated services for automatic updates, data collection, dynamic firewall, test for Internet connectivity, speed test using Netmetr.cz, and added list of OpenVPN clients to any OpenVPN servers. Based on the community feedback, we prepared for you the requested missing features in reForis. Since this release, you can see the Storage tab, the possibility of doing a factory reset from the UI and adding a registration token to use Honeypot as a Service. Some of these features were missing from an old web interface or from the previous major version of Turris OS.
Our frontend developers redesigned WebApps, a landing page where you can choose custom applications and add your own. We added the possibility of configuring the router without using the Ethernet port on your computer using a USB flash drive.
reForis
Web interface reForis is using modern open-source technologies like Bootstrap, React, and Flask. It allows us to have responsive web design and easy maintenance in the future. Unfortunately, we can not use the existing frontend parts from the old web interface Foris, and it would take a lot of time than starting from scratch. We decided to use this opportunity and start over.
In reForis, you can find since this release two new tabs – Storage and Honeypot as a Service. We also prepared new features like the possibility to do a factory reset in Administration → Maintenance. We added the option to set the hostname for your router. There are also new two packages list – RIPE Atlas SW Probe and Common passwords, which you can install in Package management. We refactored the part related to diagnostics to make it more clear and understandable with a description of what each diagnostics module does.
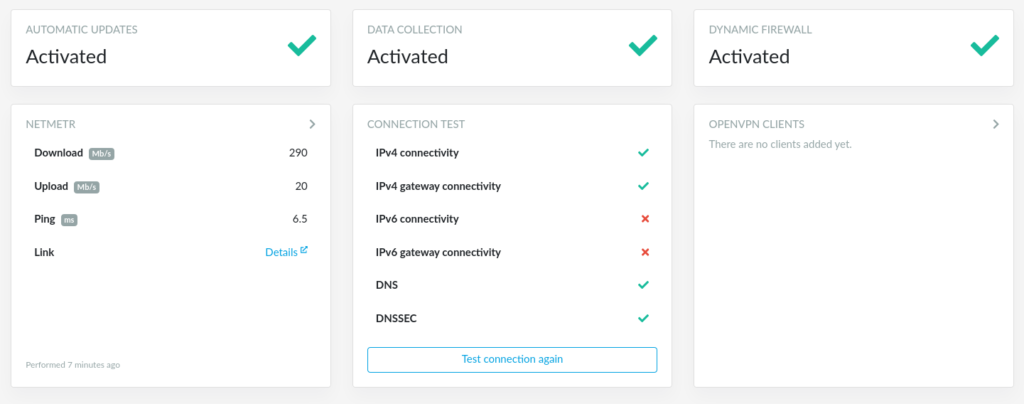
Overview
After logging into reForis, you will see Overview, which shows status about activated or disabled automatic updates, data collection, and dynamic firewall. You can also find connection tests for IPv4 and IPv6 connectivity, NetMetr.cz, and your’s added OpenVPN clients to public OpenVPN servers.
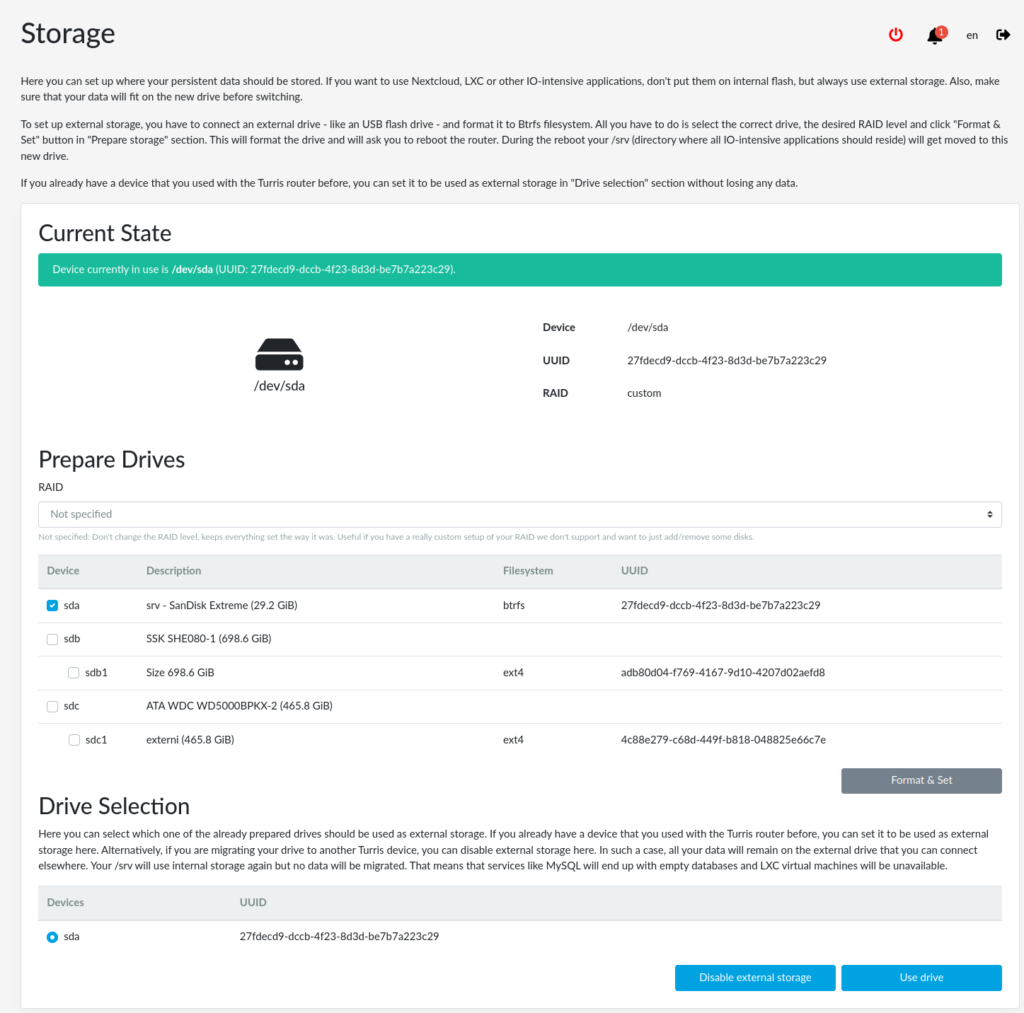
Storage tab
In this tab, you might want to configure external storage. It could be a USB flash drive, a SSD disk connected into the USB port, or even an mSATA SSD disk. You need to configure external storage if you want to install packages with the External storage label. You can find it, for example, next to LXC containers, Nextcloud, and others I/O intensive applications.
The selected external storage will be formatted to Btrfs. It will move the current folder /srv from the internal storage to external.
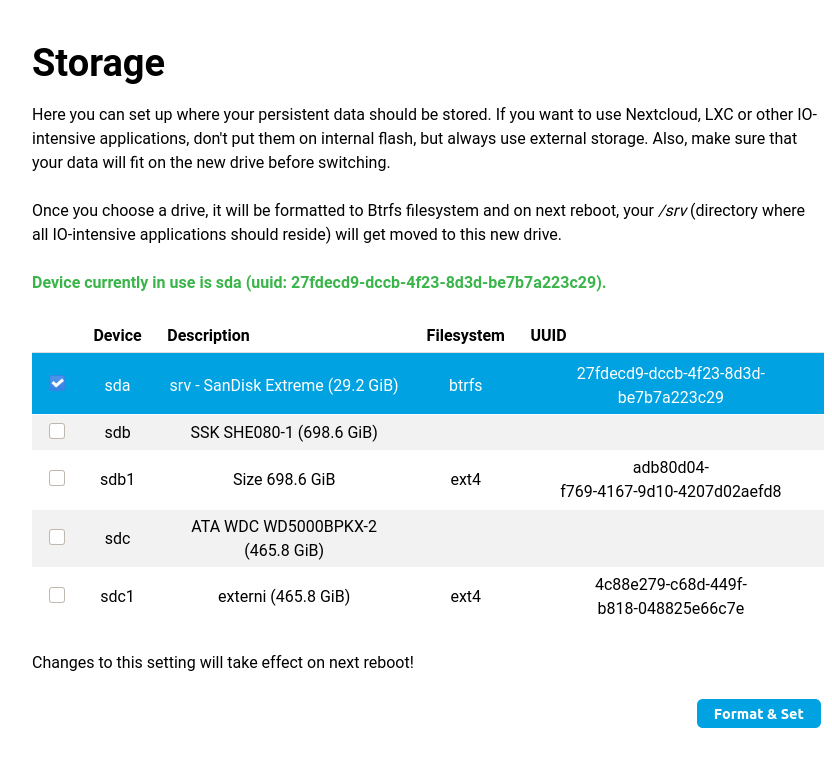
On the following screenshots, you can see the old Storage plugin in Foris and the new Storage plugin in reForis. We added an option to configure RAID and use prepared storage if you do a factory reset or something else.
Storage plugin in reForis 1.0.3
Old storage plugin from Foris
We added an option for system logs retention based on your feature requests when using the Storage plugin. All logs are stored in the router’s RAM by default and erased if you reboot the router.
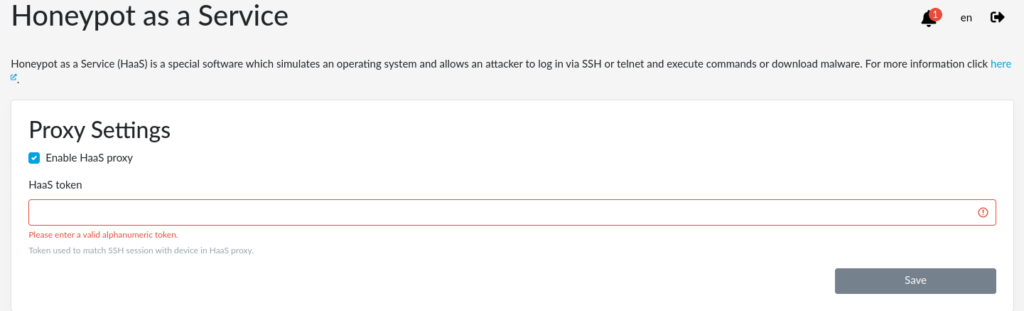
Honeypot as a Service (HaaS) tab
CZ.NIC, the Czech domain registry, runs public Honeypot as a Service. The collected data are analyzed by the national security team CSIRT.CZ. HaaS is possible to install and run on your server or your computer with a public IPv4 address. It is not required to have a Turris router. You need to register on the HaaS website or use mojeID account and follow these details.
We simplified these steps for Turris users. You need to request a token and then fill in in Honeypot as a Service tab, which you need to install using the SSH honeypot package list.
Honeypot as a Service tab in reForis
When everything is set, all SSH sessions will use the honeypot from the Internet. After some time, you can see those sessions on Honeypot as a Service website. There will be the IP address, which attacked used, credentials (login/passwords), and the attacker’s behavior like what he/she tried to do.
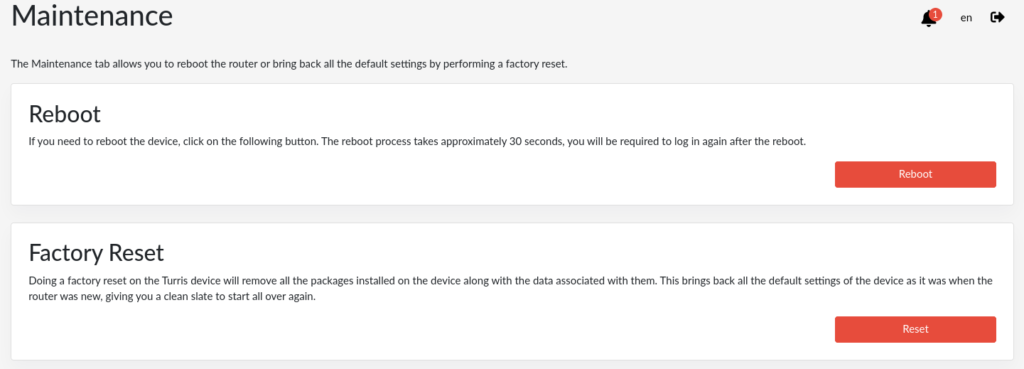
Factory reset
From web interface reForis, you can make a factory reset, which can be helpful if you want to configure your router from the beginning. It will remove all the packages you installed and modified files and restore the router into its factory state to the moment when you take the router from the original packaging.
Factory reset in the Maintenance tab
New package lists
You can see added two package lists in the package management tab – RIPE Atlas SW Probe and Common passwords.
- RIPE Atlas SW Probe is developed by RIPE NCC, the Regional Internet Register (RIR). You can be a part of the community behind RIPE Atlas. It is a worldwide network of devices that measures Internet connectivity and reachability.
- Common Passwords
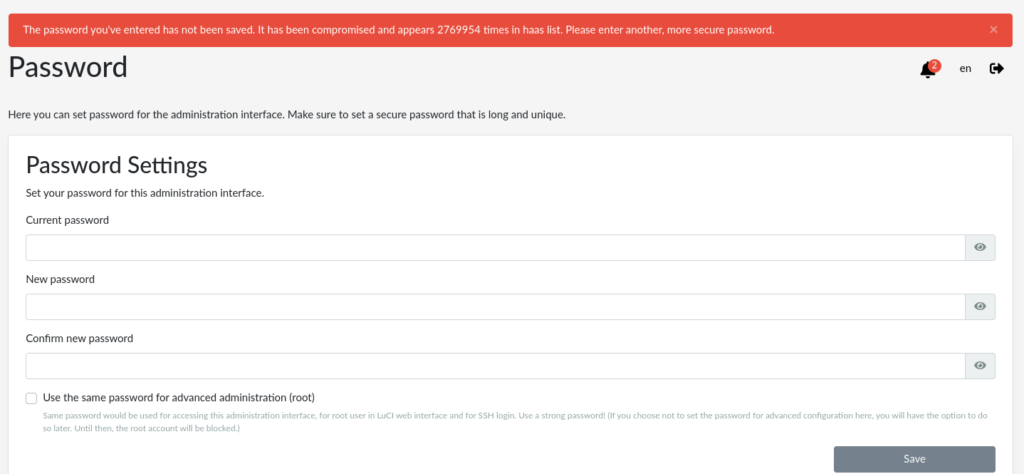
From the data collected from Honeypot as a Service, which attackers use to connect to the SSH of your router, we created a list of common passwords. Once you install this package list and while you want to change your password in reForis, it will show you a warning about the compromised password. So you need to use a new stronger password. For now, this is available only while changing the password. For Turris Shield owners, there is an exception that this feature is preinstalled by default and part of the first configuration of your device. In the future, we will add collected data from minipots.
How it looks when you want to save a compromised password
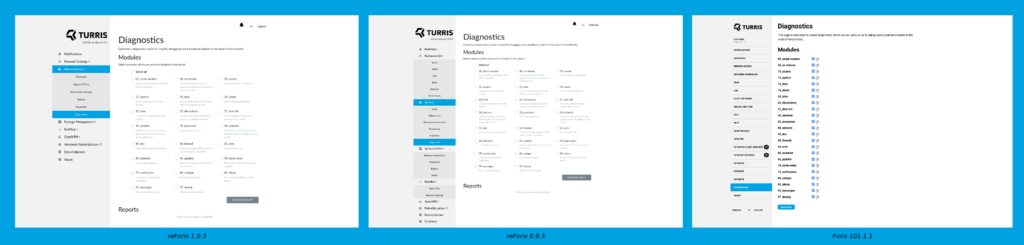
Diagnostics tab
Diagnostics are helping it while solving issues, which some users might have, and consult them with the technical support department. We take a look at how we can make diagnostics more user-friendly for you. On the screenshots, you can decide if we succeeded in making it better or not.
WebApps
We redesigned and refactored both frontend and backend parts of the landing page called WebApps, where you can choose if you want to use a Dark theme or Light theme.
 Old landing page, which you could see in previous versions of Turris OS
Old landing page, which you could see in previous versions of Turris OS
New landing page with the dark theme
List of known mini PCIe and USB drivers
We prepared for you one feature, which should help connect known USB and mini PCIe devices connected all the time to your router, such as Wi-Fi cards, LTE modems, etc. The device needs to be listed on our list of devices available on our GitLab repository for mini PCIe and USB devices. In that case, the router will automatically download the necessary drivers if there is an active Internet connection.
If you would like to add your device and help others, you need to know the vendor ID, device/product ID, and which drivers the USB or miniPCIe requires.
Ethernetless initial setup
These days, notebooks often do not have an Ethernet port. You usually need to buy a USB adapter to RJ45 to configure the router. Therefore, we decided to prepare an Ethernetless initial configuration of the router. You can configure Wi-Fi SSID and password in file medkit-config.json, put it together with the medkit to your USB flash drive, and use rescue mode 4 to reflash the router. More details about JSON syntax and about this setup can be found in our documentation.
Thanks to anyone who helped us during the testing
We appreciate anyone who joined the public testing of this release. It helped us to make this release better and fix some issues discovered by using various configurations.
We hope you like these new features, and we would like to hear your voices regarding this release on our community forum or here in the comments.