In January, we encountered slightly more attackers than in December. But overall, behavior stays the same. The number of attackers per device and victims per attacker didn’t change much. Looking back at our first report, we also had about the same amount of victims per attacker but more attackers per device. The trend for the last three months is to target about 20 Turris devices on average if you are an attacker.
We see a rising number of attempts on BitTorrent in port scans, but those might be just clients misconfigured. The first relevant port that gained popularity is Samba, aka Microsoft file sharing. No surprise there; that is quite a logical service to target. More interesting is the popularity of port 1035, which has been used in the past by various trojans. That might suggest that there is a new derivate of those spreading around.
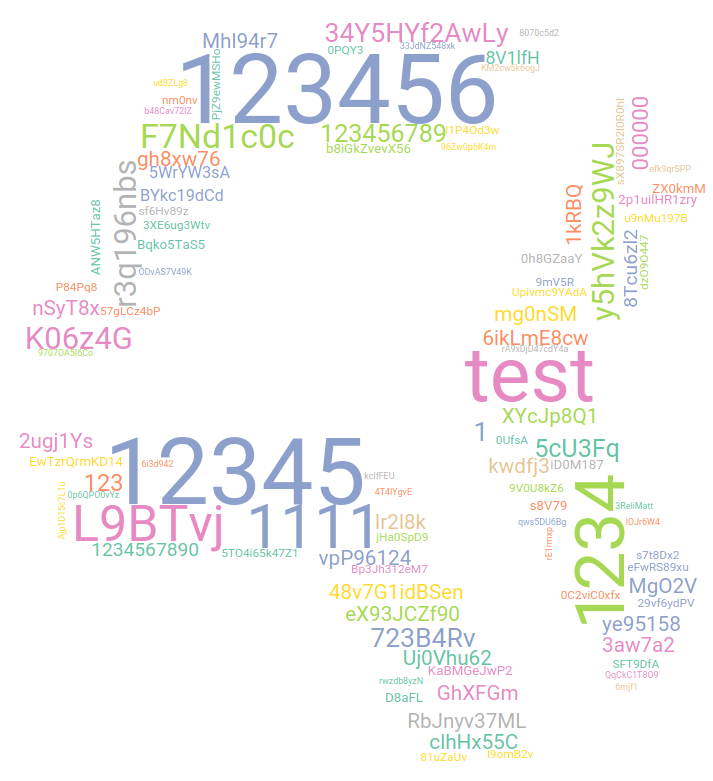
In passwords, we see a continuing trend of randomly looking passwords. After the last report, we investigated those further, and they are all attacks on SMTP, and they try multiple random passwords. Majority of those come from one IP segment – from one Iranian ISP. There are also a few extra IPs from around the world. But based on the IP allocations, those belong to various hosting providers, so the primary source of those attempts is Iran, with bounces via various hosting services worldwide.