In February, we saw about a 10% decrease in the number of unique attackers, but they were more active. Usually, we see attackers come and go, but in February, although it was fewer attackers in total, we had on average, more attackers blocked every day. This means that those attackers stayed active longer than in January.
Regarding the port attacks, we saw a decrease in attacks on many well-known ports. That is a good sign, but don’t let your guard down. An attacker has to succeed just once, while you have to repel his every attempt. The first potentially interesting port that gained some popularity among attackers is 9091. It is the default port for RPC for the Transmission BitTorrent client. That sounds like a potentially juicy target. So keep your RPC endpoints secured, and when exposing them, make sure you have a strong enough password.
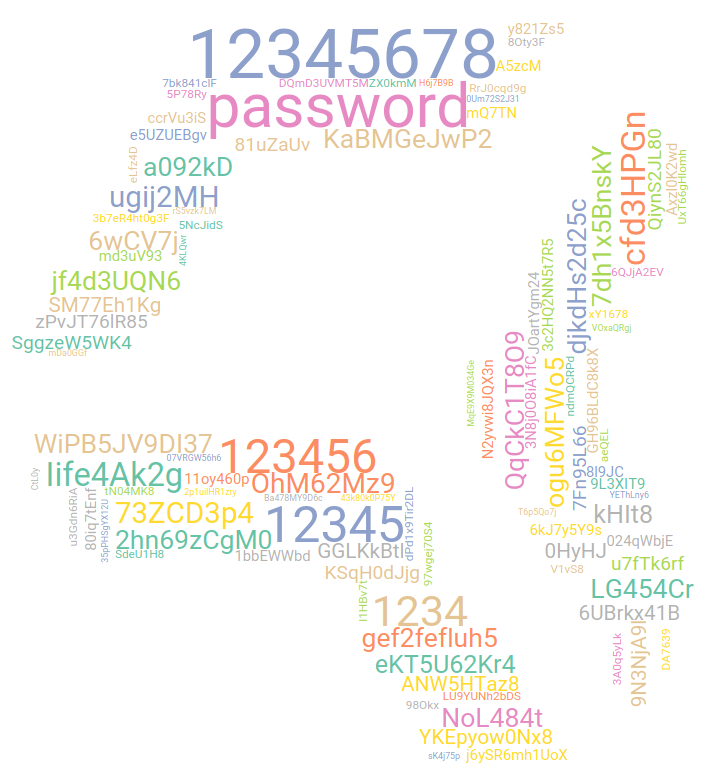
In passwords, it looks like bots figured out that many systems requests at least eight characters password, so the most popular password of February is 12345678. We also have a few well-known candidates on top, but the rest of the chart is occupied by random attacks from Iran that we already spoke about in the report for January. And although there are still a few IPs showing similar behavior, the Iranian network does an order of magnitude more attacks then everybody else combined. We also checked what the used usernames look like. To make sure it wasn’t just some random stream of data hitting our mini pots. But even though there are short usernames that look random, like v5 or h24, there is also plenty of valid usernames like admin, postmaster, or zztop and those are much more common.