Vulnerability of SOHO routers becomes a topic of analyses by various security organizations almost every week. The 2017 Symantec report shows a year-on-year increase in the number of attacks on IoT devices by 600%. The most vulnerable are unsecured routers, which often make it possible to gain easy access to each connected device. The April’s alert from the official US-CERT also tells us of the growing number of these attacks and their severity.
In our project Honeypot as a Service (HaaS), we have attempted to convert all these attacks and the results of analysts’ work into more intelligible numbers by redirecting attackers to a central honeypot. More than 2,000 users have been involved in the project supported by the Technology Agency of the Czech Republic, of which almost three-fourths are users of Turris routers.

The high number of users subsequently reflected in the volume of captured data, i.e. sessions and commandssent by the attackers to the central honeypot. The target honeypot to which the attackers were redirected registered over 73 million sessions and nearly 42 million commands during the first half of this year (some of the attackers did not send any command), see the chart.
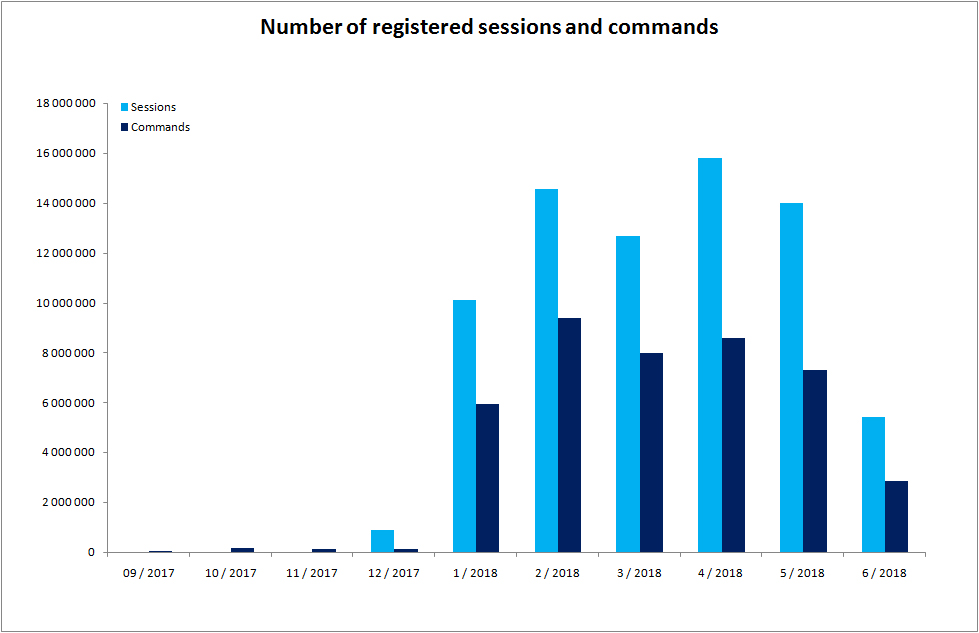
If we simplify the matter and assume that one session means one attempt to hack into the router, it will appear that every day our “Internet gateway” is a target of over 250 attacks, i.e. about ten attacks per hour. It is true that not all of these attempts are sophisticated attacks, but a more detailed analysis shows that in some cases the attacker could do significant damage.
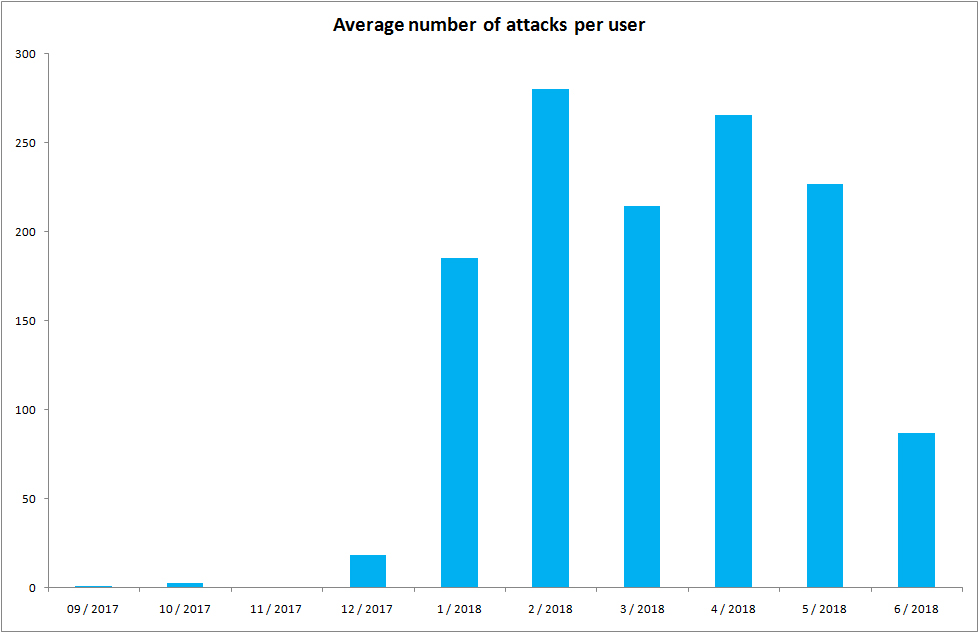
The possibility to take a closer look into the attacks was brought by the analysis of individual samples carried out in cooperation with our Taiwanese partner – Institute for Information Industry (III), under the Haas Project supported by the Technology Agency of the Czech Republic.
During the first half of this year, a total of 8,071 unique files taking more than 6 GB were uploaded to the server. Since only unique files were examined (i.e. if the file was captured in February, its capture in March does not count), the downward tendency of the captured samples makes sense.
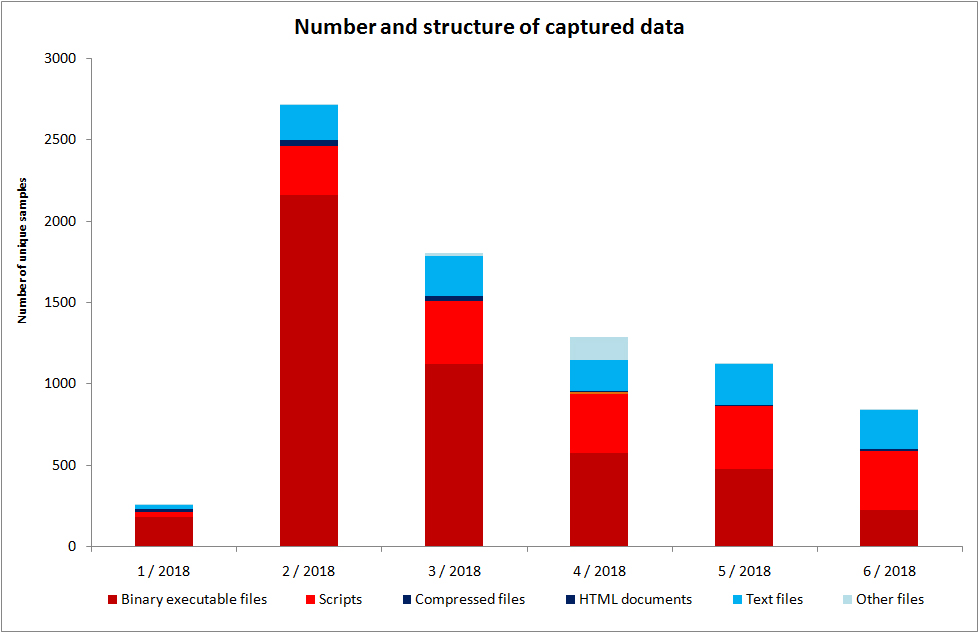
As far as target architectures are concerned, the captured binary files were very diverse – from ARM to MIPS and x86, including a variety of sub-types. The two largest files had the same beginning as installation medium of Debian 9.3 and Linux Mint 18.3, the most probable explanation for which is the attackers’ attempt to verify how much data they can store on the newly acquired machine. Another interesting finding was a 17 MB text file containing over a million domain names including 945 ones in the .CZ zone. Due to the fact that among these Czech domains were prominent those of the government, this file was sent to the National Cyber and Information Security Agency (NÚKIB).
A dynamic analysis unveiled efforts to communicate with the Command and Control (C&C) server, i.e. the botnet control computer. The communication usually started with an initialization followed by a keep-alive connection. Other captured samples attempted to connect to the so-called mining field, where their job was to extract virtual currency for the attackers. Other samples demonstrated a DDoS attack attempt, which was later turned out to be an attempt to detect the ability of an infected computer to compromise source IP addresses.
Unlike a DDoS attack, this malware attempted to send only a few packets with different source IP addresses to the address of its C&C server. If it were detected that the newly acquired computer is capable to do that, it would most likely be misused for DDoS attacks. Today, this is a very common type of attack aimed at exhausting the resources of a target that has no chance of knowing whether it is a legitimate request of a user displaying website content or artificially generated traffic.
The analysis of public honeypot data has shown that attacks on home routers are unfortunately an everyday matter. Taking care of your router’s security should be as natural as using an antivirus software.