You may have read some of our previous articles about Turris Sentinel and it’s companion – Sentinel View. Today we would like to share yet another cool feature that is available and that gives you even better feel how dangerous the internet really is.
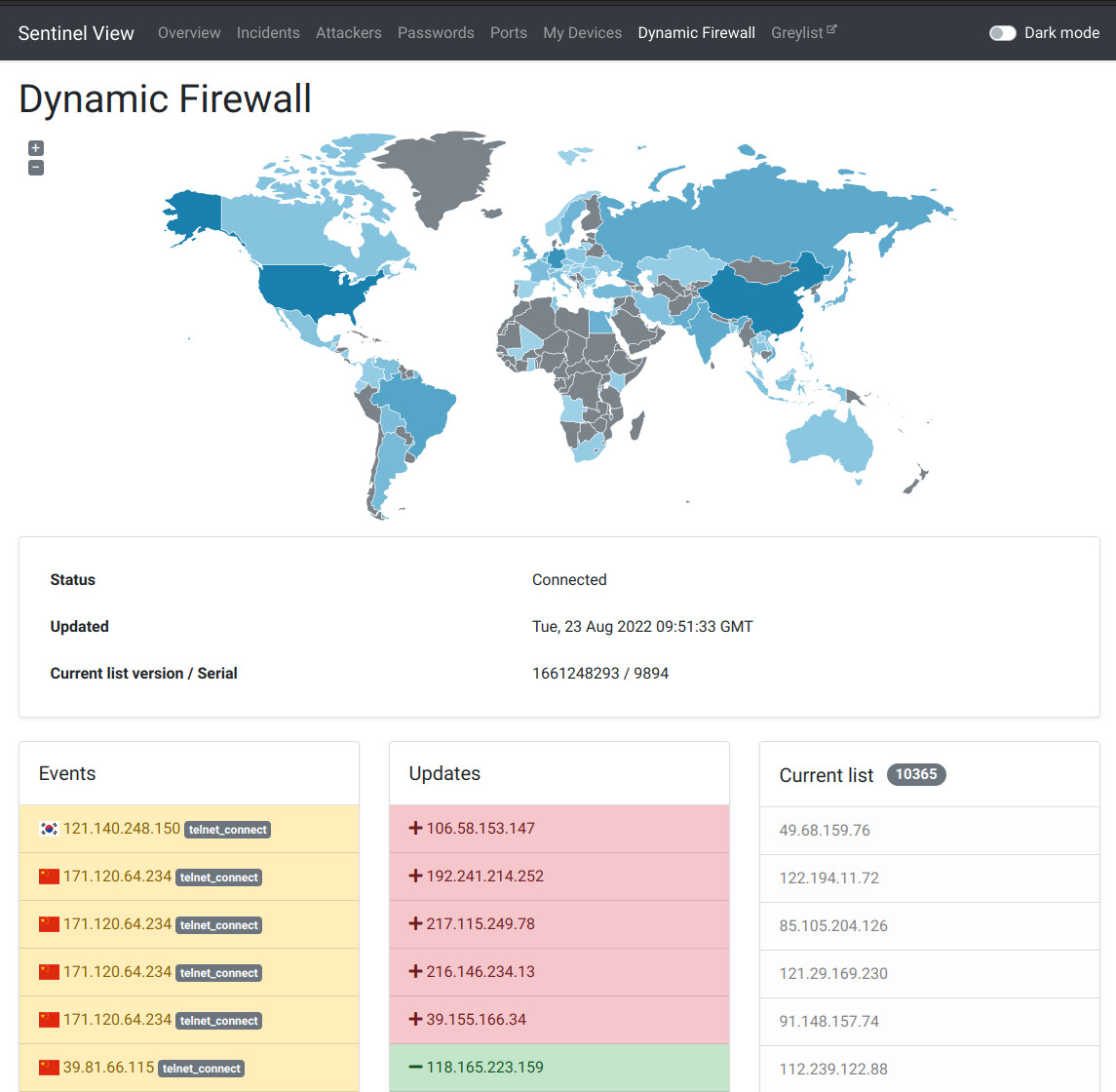
Dynamic Firewall View
You may find the feature here: https://view.sentinel.turris.cz/dynfw/
Sentinel View now shows real-time visualization of actual state of greylist.
Sentinel was not planned as simple one-purpose solution but as set of tools that will work together. There are three main outputs out of Sentinel workflow:
- Dynamic Firewall data
- “Greylist”
- Security research to avoid cybernetic threats
The simplified version would be that we collect data in minipots, send those to our server. Server than determines whether the address is dangerous and adds it to “Greylist” while also alerts Dynamic Firewall on each Turris device, which than updates it’s firewall accordingly. To explain Dynamic Firewall View we have to start with minipots.
minipots
Honeypot is a program that mimics a service, thus it is a fake server. Program that pretends to offer service for a protocol. We call ours minipots just to emphasize their load, size and how feature-complete they are. As of now we operate Telnet, FTP, HTTP and SMTP minipots on our routers. Attacker tries to connect to this fake server and is asked for his credentials. Nothing more. Adding more complexity might provide the wannabe attacker with more attack vectors. Based on that event we now have IP address of attacker, credentials that he tried to use and other detailed data.
lurking danger
The data that are collected on router are sent to our servers. Server determines whether IP address is malicious/dangerous based on some statistical computations. It is important to distinguish between when you make an error and try to login to your device from the internet forgetting about minipots and somebody have some hostile intentions. Through course of time we believe we tuned our systems well, to make this distinction just, but it is neverending process and from time to time we find some exceptions that we need to take into account, but the overwhelming majority of the decisions seem correct. This results to…
Greylist
Or the list of potentially malicious players. The set of addresses is created in the real-time from data fed by minipots and other sources. It is published once a day as a snapshot, but the list is updated dynamically, so addresses are being added and removed constantly. Dynamic Firewall Dynamic Firewall simply blocks any request on any service from IP address that is on the greylist. It is simple as that. Tough it is the crucial part of protection and it does its work, it would not without the whole ecosystem. It has a direct connection with the server maintained Greylist and it receives the updates of malicious IP addresses in the real-time. the View
 |
Event box shows you the actions on routers with flag of country of attacker’s origin, IP address and protocol they using. |
| Updates box shows you updates to the greylist. Simply put whenever the address is added (red box) or removed (green box). |
what’s next
I am not gonna make any spoilers. We will release major feature that you will like next month along with some minor bug fixes regarding UI.
Keep connected!